Introduction
In a previous blog post (https://www.shapeblue.com/api-driven-console-access/) we described the latest improvements around VNC console access in CloudStack 4.18. These improvements included switching it to an API-driven approach, and introduced a way to secure WebSocket traffic between the CPVM and end-users, whilst the traffic between the CPVM and hosts remained decrypted.
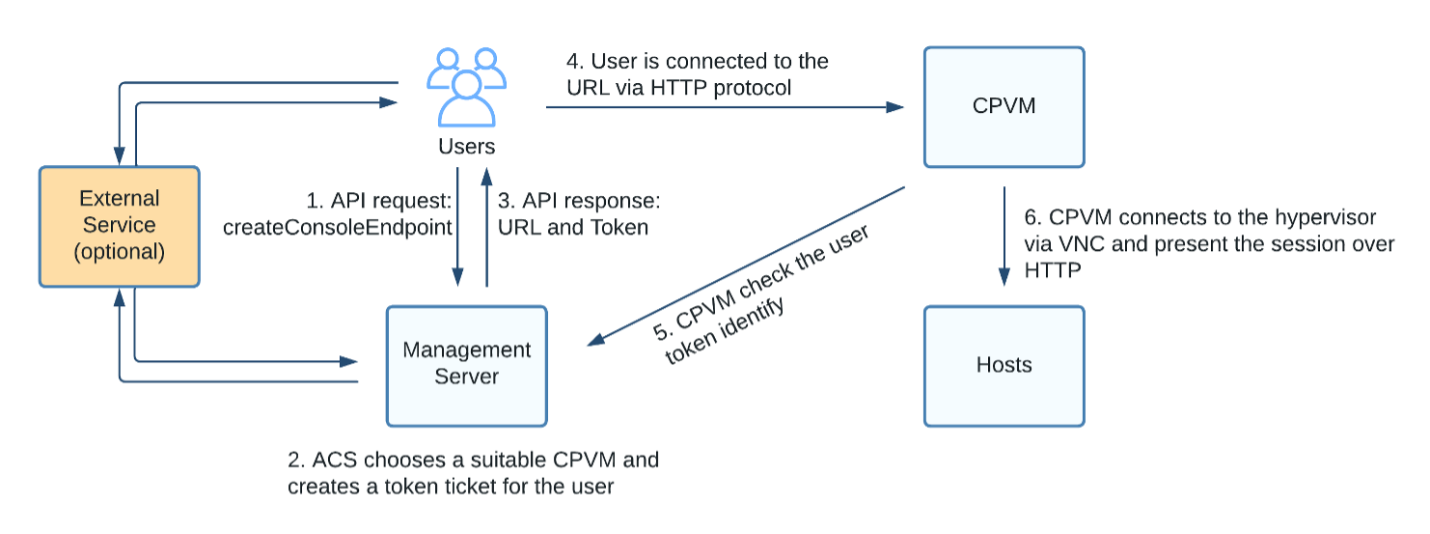
This blog post explains how we can also secure the traffic between the CPVM and KVM hosts, allowing complete security around the Instance console access. This feature is only supported by the KVM hypervisor at this time.
Secure VNC access
This feature allows securing Instance console access through CloudStack to the virtual machines running on KVM. Secure access is achieved through the generated certificates for the CA Framework in CloudStack, which provides mutual TLS connections between agents. These certificates are used to also secure the connection between the console proxies and the VNC ports for Instance console access.
For this, we use a simple configuration of an existing QEMU / libvirt mechanism to encrypt the VNC traffic and secure the communication. By default, VNC communication is not encrypted.
Background: QEMU / libvirt configuration for VNC encryption
QEMU provides a mechanism to secure VNC traffic for the Instance’s console access, through certificate authority and server certificates. CloudStack already supports the Certificate Authority method on the KVM, CPVM and SSVM agents. To configure the VNC connections for TLS using the existing certificates it is necessary to copy the CA Certificate, Server Certificate and Server Certificate Private Key to each KVM host at ‘/etc/pki/libvirt-vnc’ directory considering the exact name for the each file as below:
| Resource | File name |
| CA Certificate | ca-cert.pem |
| Server Certificate | server-cert.pem |
| Server Certificate Private Key | server-key.pem |
After setting up the certificates, modify the /etc/libvirt/qemu.conf file as below:
| Property | Value |
| vnc_tls_x509_verify_dir | /etc/pki/libvirt-vnc |
| vnc_tls | 1 |
| vnc_tls_x509_verify | 1 |
To ensure the qemu process can access the certificates directory, the necessary privileges (if needed) are provided. After that, the last step is a restart of the libvirt daemon service. The complete guide can be found at https://wiki.libvirt.org/page/VNCTLSSetup
CloudStack automatic VNC encryption on KVM hosts
This feature works along with the CA Framework in CloudStack. The above configuration is automatically triggered on the KVM hosts when the hosts are secured with the CA Framework certificates:
• The provisionCertificate API is extended, to enable TLS on VNC
• When a new host is added and it is provisioned with a certificate, TLS will also be enabled for VNC
• After provisionCertificate API execution, a host is secured with VNC encryption as described in section 2.1.1
• The running VMs on a secured host will continue to be VNC unencrypted unless they are rebooted, stopped, or started.
• New VMs created on a secured host will be VNC encrypted.
CloudStack access to secure VM consoles
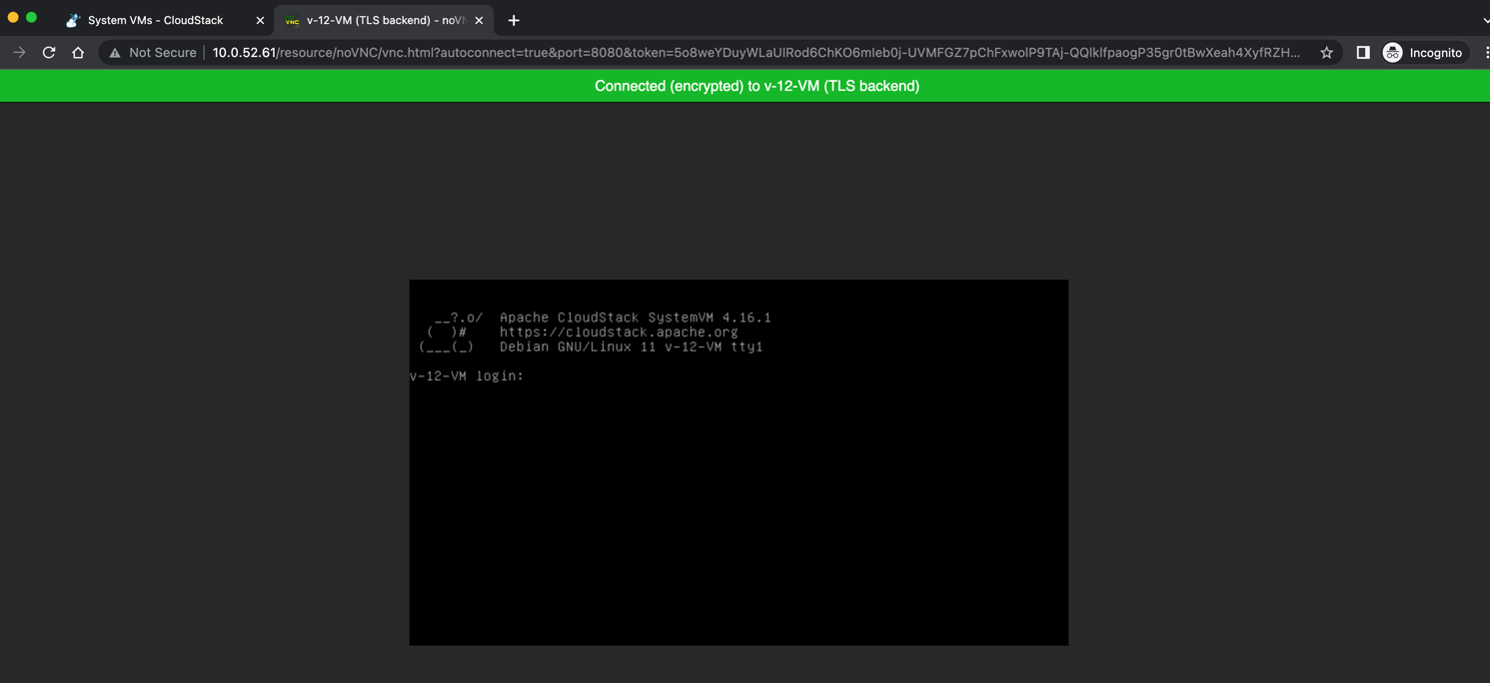
Once the administrator concludes the certificates provisioning on Cloudstack, the VM console access for new VMs on the hosts will be encrypted. CloudStack displays the console of the virtual machines through the noVNC viewer embedded in the console proxy System VMs.
The CloudStack users will notice the encrypted VNC sessions display a green bar stating the session is encrypted as in the image below. Also, the tab title includes ‘(TLS backend)’ when the session is encrypted.
Conclusion
This new feature is a part of Apache CloudStack 4.18. It extends the security in the communication between the CPVM and the KVM hosts in the CloudStack management network, reducing risks when a console session of the Instance is initiated by the users.
Nicolas Vazquez is a Senior Software Engineer at ShapeBlue and is a PMC member of the Apache CloudStack project. He spends his time designing and implementing features in Apache CloudStack and can be seen acting as a release manager also. Nicolas is based in Uruguay and is a father of a young girl. He is a fan of sports, enjoy playing tennis and football. In his free time, he also enjoys reading and listening to economic and politics materials.