In this post, Rohit Yadav, Software Architect at ShapeBlue talks about his work on the recent implementation of SAML 2.0 based Single Sign-On (SSO) and Single Log-Out (SLO) for Apache CloudStack
As part of the ShapeBlue Software Engineering Team, I work on both CloudStack feature requests for our customers and vendor integrations for CloudStack. However, we do sometimes identify features that we feel are just simply missing from CloudStack. They’re missing because no one customer/user has ever had a strong enough need to either develop them or to ask a company like ours to develop them; these are the “nice to haves”. So, we’ve recently been working internally here to develop some of these as part of our overall commitment to the Apache CloudStack project.
Apache CloudStack has its own cookie and key based authentication, and a special pre-shared secret key SSO mechanism but has no support for standard authentication protocols or mechanism such as SAML 2.0, OAuth2, etc. Many large organisations who may use such open and standard single sign on mechanisms cannot natively integrate the with CloudStack . This is not the first time this has come up: last year John Burwell also gave a talk on integrating SSO in CloudStack.
So, we set to work on fixing this.
SAML 2.0 is a widely used standard for exchanging authentication and authorization data between security domains. We found that a lot of CloudStack enterprise users have SAML 2.0 compliant authentication infrastructures so we started refactoring the CloudStack authentication layer to support integration of organisation specific custom authentication mechanisms which can then be implemented as CloudStack plugins.
Refactoring the authentication layer was a pretty straight forward task and it is briefly documented on the project wiki and we then used the re-factored authentication layer to implement a SAML service provider as a plugin, the functional spec of this work can be read here.
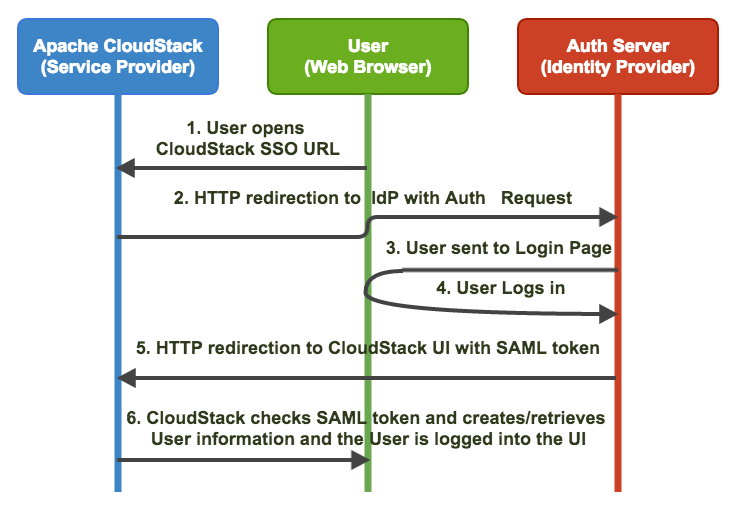
In SAML terminology, CloudStack is a Service Provider (SP) that means it’s the service that users would want to access and the organization would have their own Identity Provider (IdP) which is an authentication and authorization service backed by a user listing/store such as LDAP, AD etc. For the implementation of the plugin, we used OpenSAML which is an opensource Java library that provides building blocks to implement SAML IdP or SP. For testing the service provider implementation we used Feide OpenIdP. The flow diagram below explains the SAML 2.0 authentication workflow that uses SAML 2.0’s HTTP redirection binding.
The work can be found in the master branch of Apache CloudStack and will be available in Apache CloudStack 4.5.0 release, in future. However, we could back-port it if we see demand. You may read the latest administration docs for configuring and using SAML 2.0 authentication.
About the Author
Rohit Yadav is a Software Architect at ShapeBlue and an Apache CloudStack Committer. He is the author and maintainer of CloudMonkey, and has contributed and worked on various parts of CloudStack such as Auth layer and SAML plugin, API layer, authentication, database, accounts, KVM, virtual router, systemvms and the maven build system. He was also behind DevCloud2, the API discovery service and developed methods to build and export systemvms using VirtualBox.
Find out more about ShapeBlue’s CloudStack Software Engineering Services
Rohit Yadav oversees the Software Engineering function at ShapeBlue, providing leadership and mentorship to our ever-growing Engineering Team. He has been a PMC member of the project since 2015. Rohit is the author & maintainer of the CloudStack CloudMonkey project and has been instrumental in the development of many of CloudStack’s flagship features. Rohit regularly speaks at events, focussing on developer access to the project, and has also mentored Google Summer of Code students.