Introduction
Two-Factor Authentication (2FA) is an authentication method where a user is authorised to login into a system only after successfully presenting two pieces of data, or factors. Something that the user knows plus something which the user possesses.
Apache CloudStack 4.18 introduces a 2FA framework designed to bolster security when users access the platform. This feature can be enabled globally, by Domain, or for specific users, allowing operators to apply compliance policies for CloudStack access. The framework is also designed to be easily expandable, making it simple to incorporate additional 2FA methods in the future that align with security and compliance policies.
Watch a presentation for the new security method of authentication:
Using Two-Factor Authentication
With the latest version of Apache CloudStack, users can now leverage Timed-based One Time-Password (T-OTP) authenticators and static PIN as part of the 2FA authentication process. If 2FA is enabled for a user, they will then need to refer to the 2FA code generated by a T-OTP application (such as Google Authenticator) and enter it to finalize the login to the CloudStack portal. Those who use a static PIN must enter the PIN generated during the setup process.
Enabling Two-Factor Authentication
CloudStack 4.18 introduces new options for Root Admin and Domain Admin to configure 2FA to enforce security on user accounts. The following Global Settings are available for enabling and configuring 2FA and can be applied globally and at the Domain level:
| Global Setting | Default values | Description |
| enable.user.2fa | false | Determines whether 2FA is enabled or not |
| mandate.user.2fa | false | Determines whether to make the 2FA mandatory or not for the users |
| user.2fa.default.provider | totp | The default user 2FA provider plugin. Eg. totp, staticpin |
‘enable.user.2fa’ in Apache CloudStack allows administrators to make 2FA optional for users. When ‘mandate.user.2fa’ is also enabled at the global level or for a specific domain, all users are forced to use 2FA to login in CloudStack. If the user has not configured 2FA yet, they must set it up in a designated panel immediately after entering their password before completing the login process in the CloudStack portal.
Currently, CloudStack supports two different providers: T-OTP and Static PIN. The provider can be selected using the option ‘user.2fa.default.provider’ in Global and Domain Settings.
Additionally, 2FA can utilize the following settings:
| Global setting | Default values | Description |
| user.2fa.issuer | CloudStack | Name of the issuer of two factor authentication. |
| user.2fa.provider.exclude | Extensions to exclude from being registered. | |
| user.2fa.providers.order | totp,staticpin | The order of precedence for the extensions (available only at Global Settings). |
The option ‘user.2fa.issuer’, controls the 2FA name to be shown on the authenticator app.
To prevent users from using a specific 2FA provider, it is possible to configure the exclusion by setting the ‘user.2fa.provider.exclude’ option and it is available only in Global Settings.
The ‘user.2fa.providers.order’ option specifies the order of precedence for initializing 2FA providers internally within CloudStack. It also displays the list of providers to users in the specified order. This option is available only in Global Settings.
User Setup
With 2FA already enabled, let’s consider scenarios with mandate.user.2fa disabled and enabled.
mandate.user.2fa is disabled
1. Navigate to the user profile:
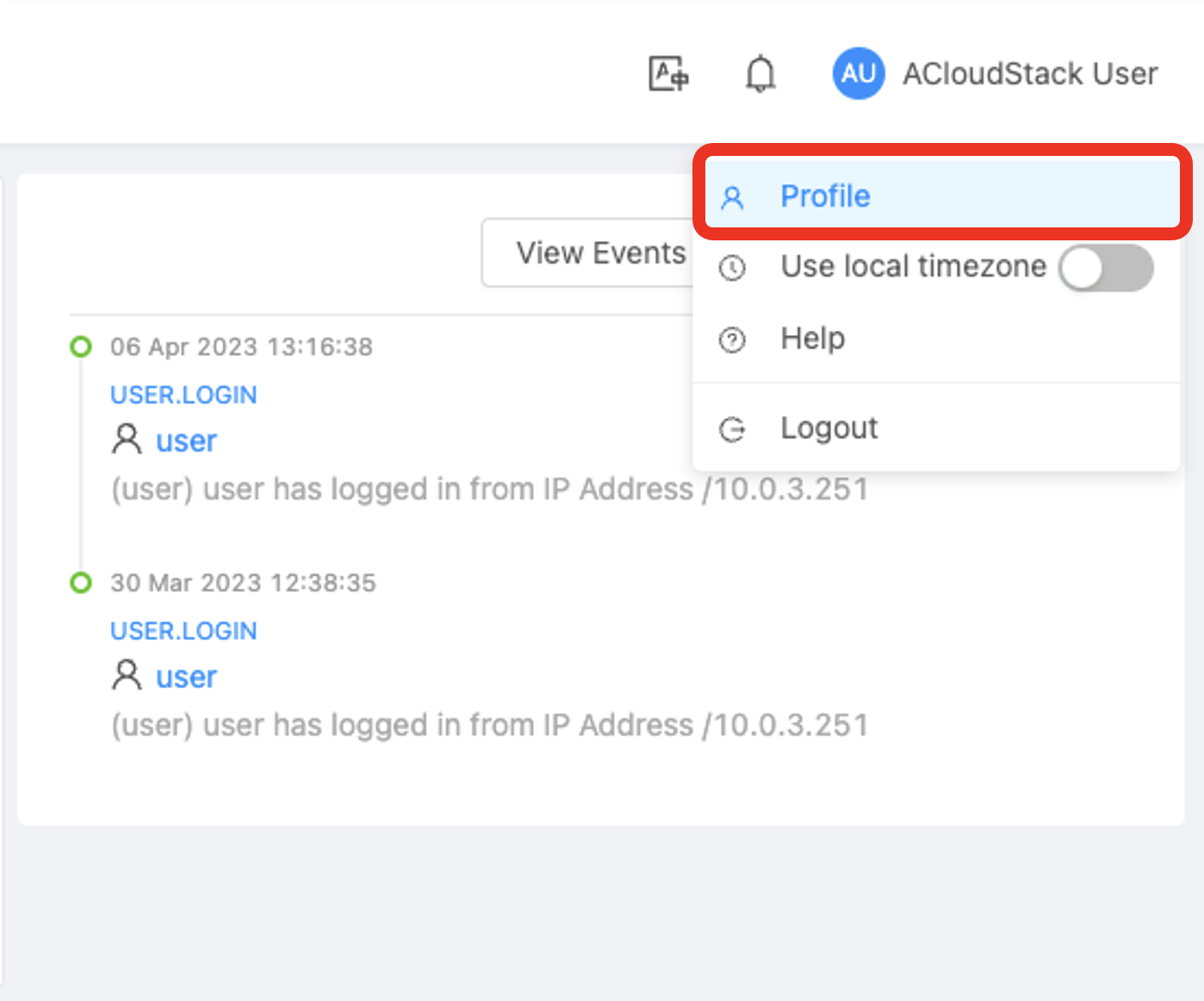
2. Click on the “Setup Two Factor Authentication” button:
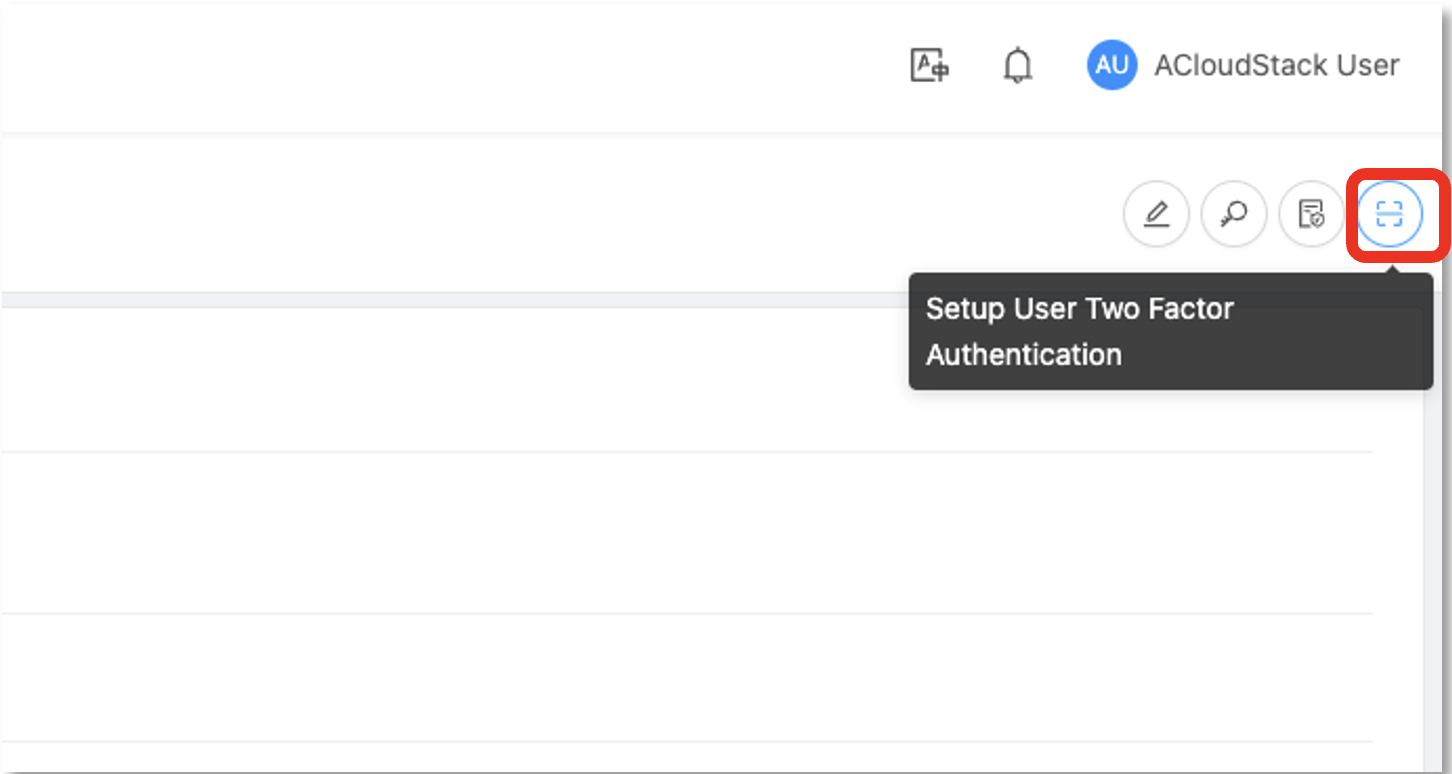
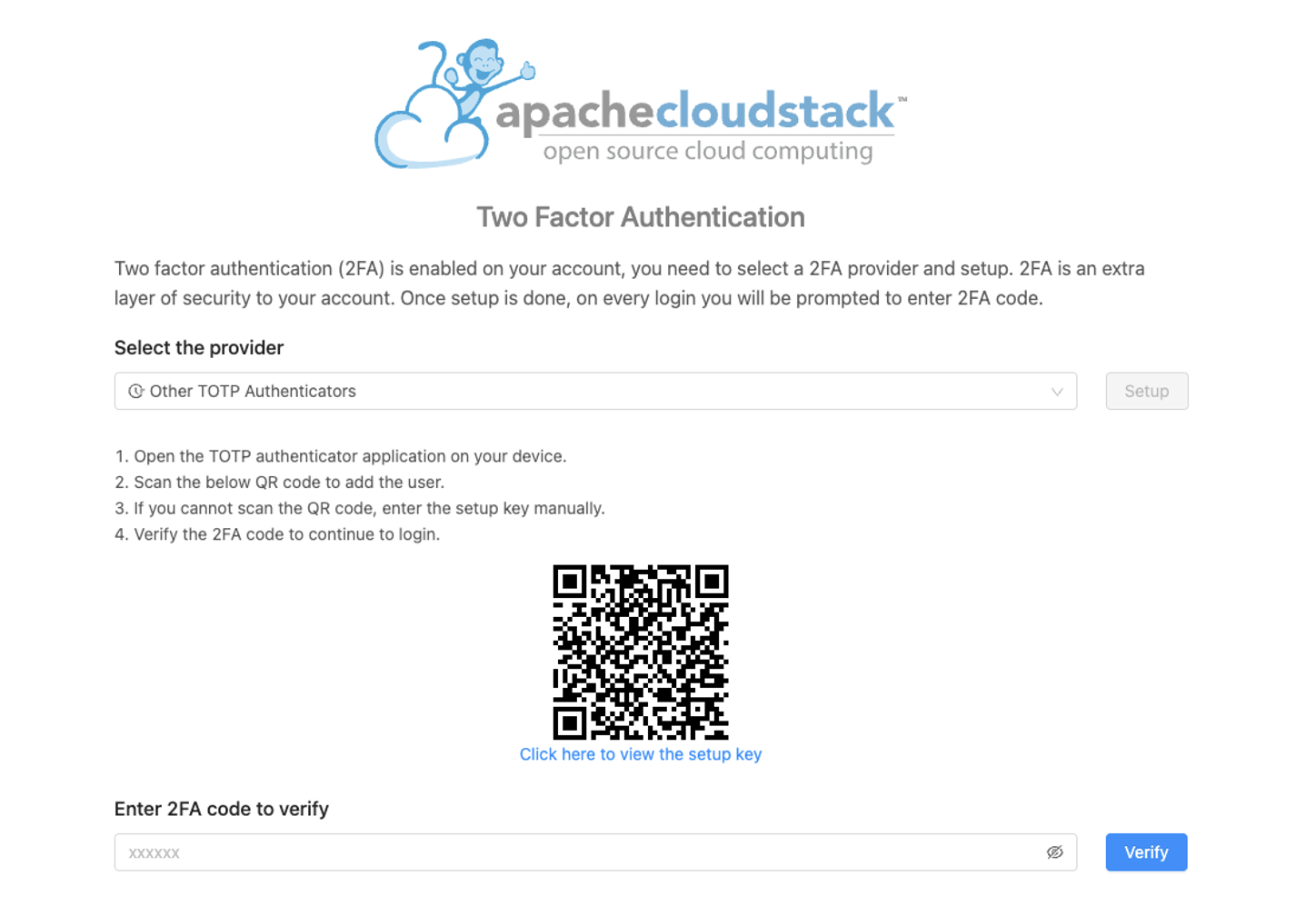
3. Select the “Other TOTP Authenticator” provider in the list and then click on the “Setup” button:
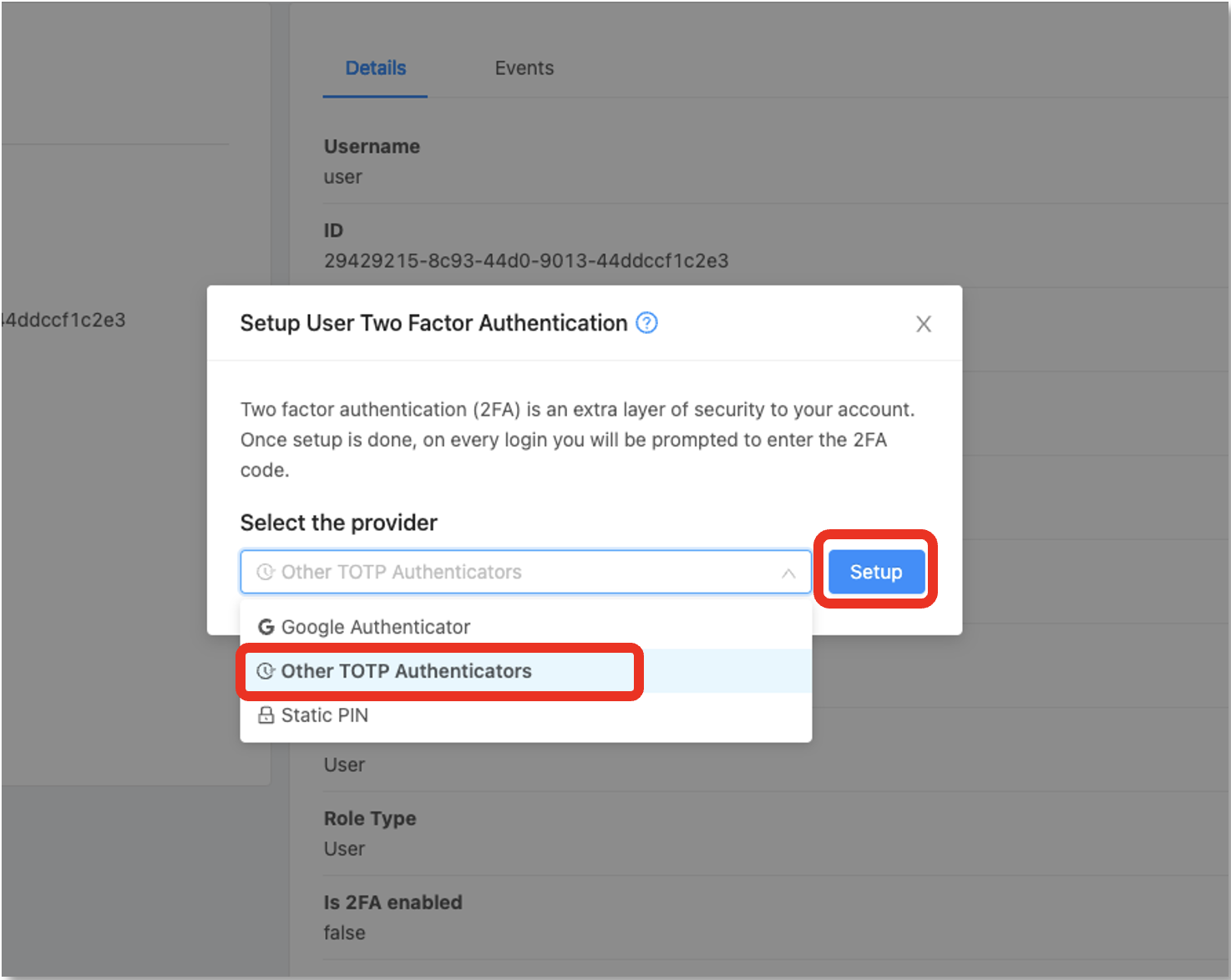
4. To set up two-factor authentication, begin by opening your preferred TOTP app on your smartphone. Next, either scan the provided QR code using your smartphone camera or click the “Click here to view the setup key” link below to show the code and add the account to your app. Afterwards, input the 2FA code displayed in the app and press the “Verify” button to enable it:
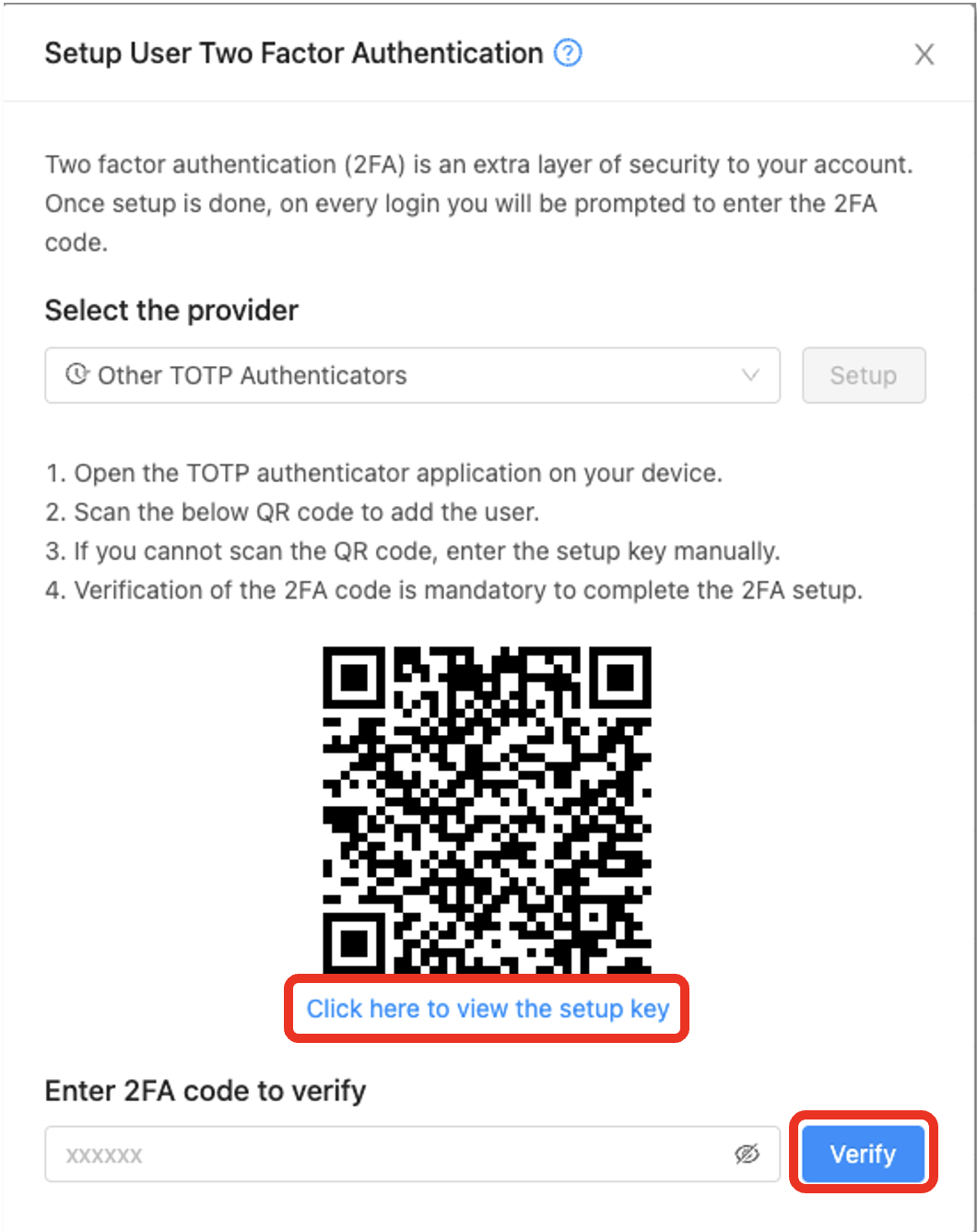
5. Logout and log in again to test 2FA for the user:

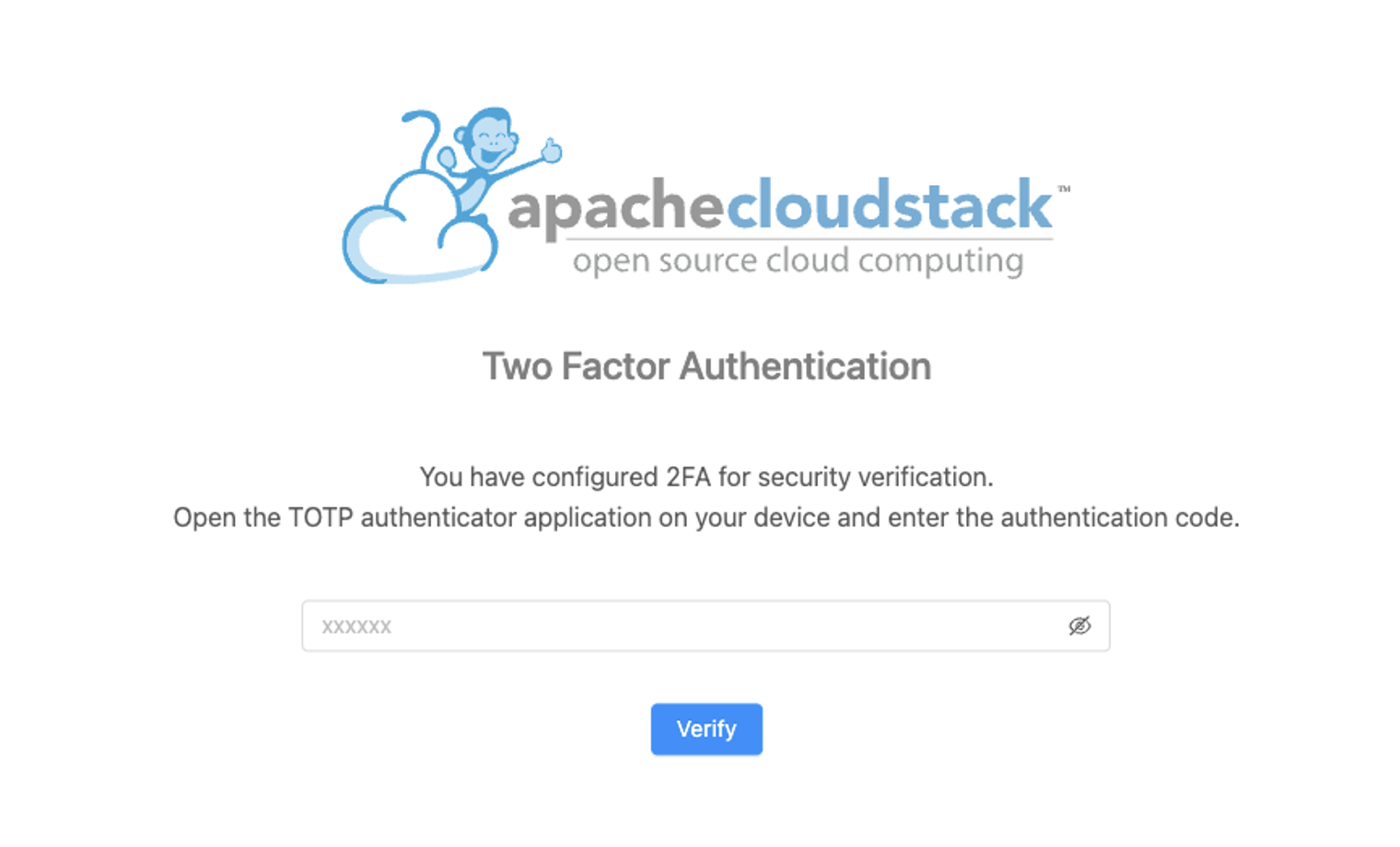
6. After the first-factor authentication is passed (the user password is matched), the second-factor will be requested. Insert the 2FA code from your app and click on the “Verify” button:
mandate.user.2fa is enabled
Considering the option “mandate.user.2fa” is enabled, after the user login, will be asked to the user to set up the second factor to authentication. It is very similar to the previous steps but in this case, the user will not have the option to disable two-factor authentication.
Conclusion
Implementing two-factor authentication (2FA) strengthens security measures, particularly since Time-based One-Time Passwords (TOTP) offer better protection than traditional OTP Authentication methods. By adopting 2FA in Apache CloudStack 4.18, companies can not only meet compliance standards but also ensure secure user access to the cloud orchestration portal. This approach makes it easier for users to understand the benefits of enhanced security and the importance of meeting compliance requirements.
Harikrishna works at ShapeBlue as a Software Engineer, and is also engaged with active development of new features and capabilities for the Apache CloudStack project. He has been working on CloudStack since 2012 and is a committer in this project. Before joining ShapeBlue, Harikrishna worked for Citrix Systems and Accelerite. He holds an M.Tech in Computer Science and Engineering from IIT-Madras.
You can learn more about Harikrishna and his background by reading his Meet The Team blog.





