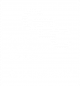CloudStack has more than 600 APIs which can be allowed / disallowed in different combinations to create dynamic roles for the users. The aim of this feature is more effective use and management of these dynamic roles, allowing CloudStack users and operators to:
- Import and export roles (rule definitions) for the purpose of sharing.
- Create a new role from an existing role (clone and rename) to create a slightly different role.
- Use additional built-in roles (to quickly create read-only and support users and operators), such as:
- Read-Only Admin role: an admin role in which an account is only allowed to perform any list / get / find APIs but not perform any other operation or changes to the infrastructure, configuration or user resources.
- Read-Only User role: a user role in which an account is only allowed to perform list / get / find APIs who may only be interested in monitoring and usage for instance.
- Admin-Support role: an admin role in which an admin account is limited to perform day-to-day tasks, such as creating offerings, but cannot change physical networks or add / remove hosts (but can put them in maintenance).
- User-Support role: a user role in which an account cannot create or destroy resources (any create*, delete* etc. APIs are disallowed) but can view resources and perform operations such as start / stop VMs and attach / detach volumes, ISOs etc.
The existing role types (Admin, Domain Admin, Resource Admin, User) remain unchanged. This feature deals purely with the Dynamic Roles which filter the APIs which a user is allowed to call. The default roles and their permissions cannot be updated or deleted.
Cloning a role
An existing role can be used to create a new role, which will inherit the existing role’s type and permissions. A new parameter: roleid is introduced in the existing createRole API which takes the existing role id as the input, to clone from. The new role created can be modified to create a slightly different role later.
Example API call:
http://<ManagementServerIP>:8080/client/api?command=createRole&name=TestCloneUser&description=Test%20CloneUser01&roleid=ca9871c2-8ea7-11ea-944e-c2865825b006
The Add Role dialog screen shown below is used to create a new role by selecting an existing role:
 Import role and export rule definitions
Import role and export rule definitions
A role can be imported with its rule definitions (rule, permission, description) using a new API: importRole with the following parameters:
- name (Type: String, Mandatory) – role name
- type (Type: String, Mandatory) – role type, any of the four role types: Admin, Resource Admin, Domain Admin, User
- description (Type: String, Optional) – brief description of the role
- rules (Type: Map, Mandatory) – rules set in the sort order, with key parameters: rule, permission and description
- force (Type: Boolean, Optional)- whether to override any existing role (with same name and type) or not, “true” / “false”. Default is false
Example API call:
http://<ManagementServerIP>:8080/client/api?command=importRole&name=TestRole&type=User&description=Test%20Role&rules[0].rule=create*&rules[0].permission=allow&rules[0].description=create%20rule&rules[1].rule=list*&rules[1].permission=allow&rules[1].description=listing&force=true
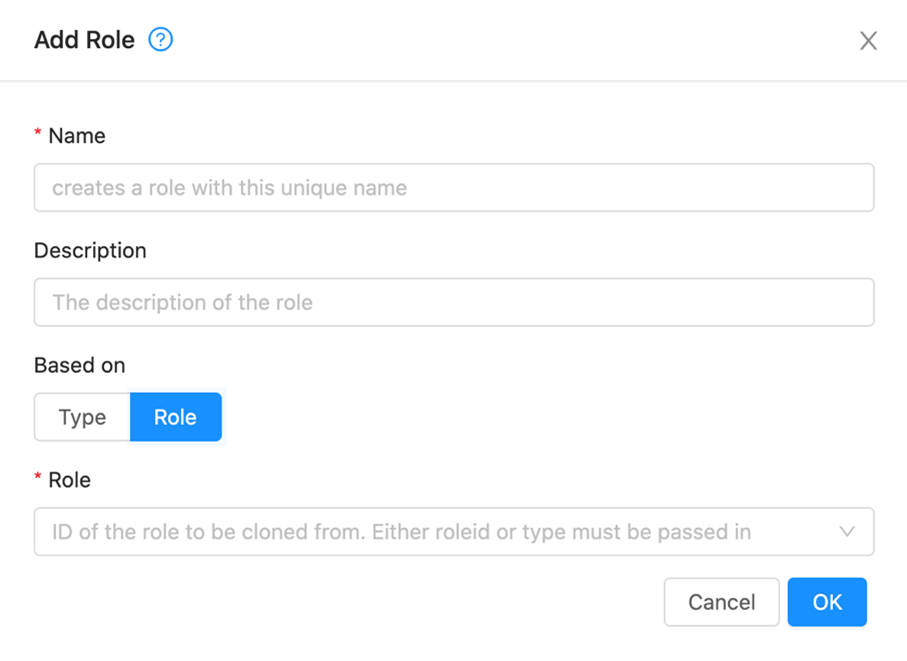
The import role option in the Roles section of the UI opens up the Import Role dialog screen below. Here you can specify the rules with a CSV file with rule, permission and description in the header row, followed by the rule values in each row:
The imported rule definitions are added to the rule set of the role. If a role already exists with the same name and role type, then the import will fail with a ‘role already exists’ message, unless it is forced to override the role by enabling the force option in the UI or setting the “force” parameter to true in the importRole API.
The ‘Export rules’ operation for a role is allowed at the UI level only, at the rules details as shown below. This operation fetches the rules for the selected role and exports to a CSV file. The exported rule definitions file can be thereafter used to import a role.
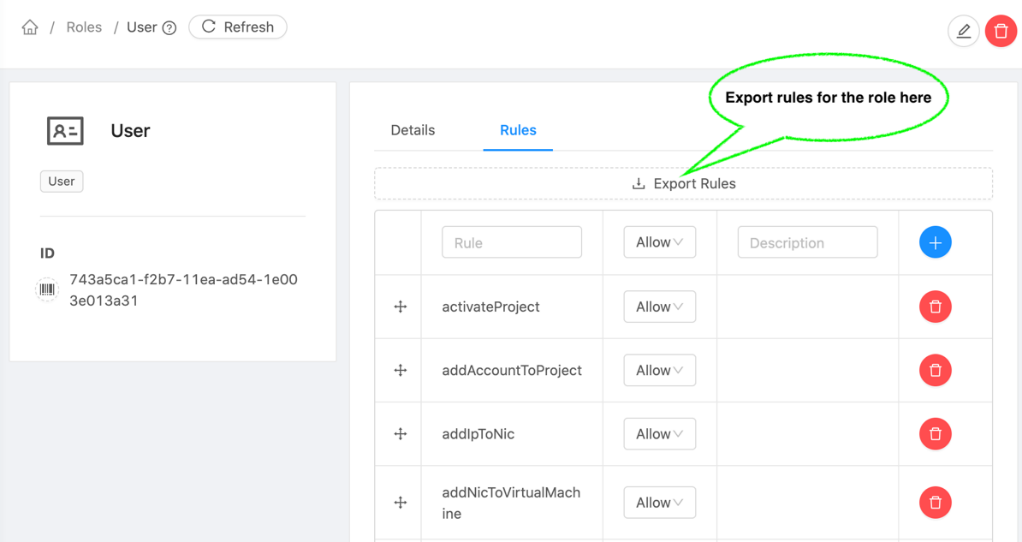
The rule definitions import / export file (CSV) contains details of role permissions. Each permission is defined in a row with comma-separated rule, permission (allow/deny) and description values. The row sequence of these permission details is considered to be the sort order, and the default export file name is “<RoleName>_<RoleType>.csv”.
Example CSV format:
rule,permission,description
<Rule1>,<Permission1>,<Description1>
<Rule2>,<Permission2>,<Description2>
<Rule3>,<Permission3>,<Description3>
…and so on, where:
- Rule – Specifies the rule (API name or wildcard rule, in valid format)
- Permission – Whether to “allow” or “deny”
- Description – Brief description of the role permission (can be empty)
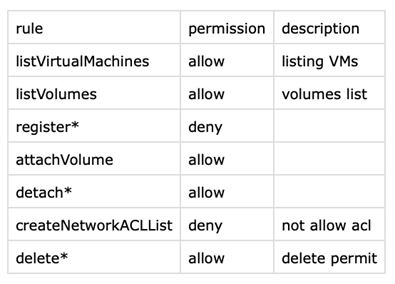
Example file (.csv), for TestUser with User role, TestUser_User.csv contains:
rule,permission,description
listVirtualMachines,allow,listing VMs
listVolumes,allow,volumes list
register*,deny,
attachVolume,allow,
detach*,allow,
createNetworkACLList,deny,not allow acl
delete*,allow,delete permit
TestUser_User.csv shown in a spreadsheet (for clarity):
New built-in roles
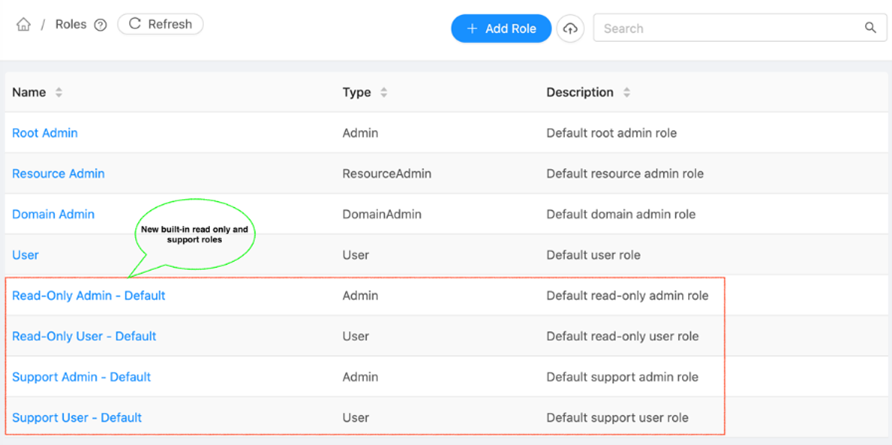
New read-only and support roles (with pre-defined sets of permissions) for user and operator, namely Read-Only Admin, Read-Only User, Support Admin and Support User have been added to quickly create read only & support users and admins.
CloudStack doesn’t allow any modifications to built-in roles (new & existing), i.e. these default roles and their permissions cannot be updated, deleted or overridden. The image below shows new and existing built-in roles:
The following permissions are applicable for these roles:
- Read-Only Admin: an admin role in which an account is only allowed to perform all list APIs, read-only get and quota APIs.
- Read-Only User: a user role in which an account is only allowed to perform list APIs, read-only get and quota APIs which has user level access.
- Support Admin: an admin role in which an account is only allowed to perform creating offerings, host/storage maintenance, start/stop VMs, Kubernetes Cluster, attach/detach volumes, ISOs.
- Support User: a user role in which an account is only allowed to perform, start/stop VMs, Kubernetes Cluster, attach/detach volumes, ISOs.
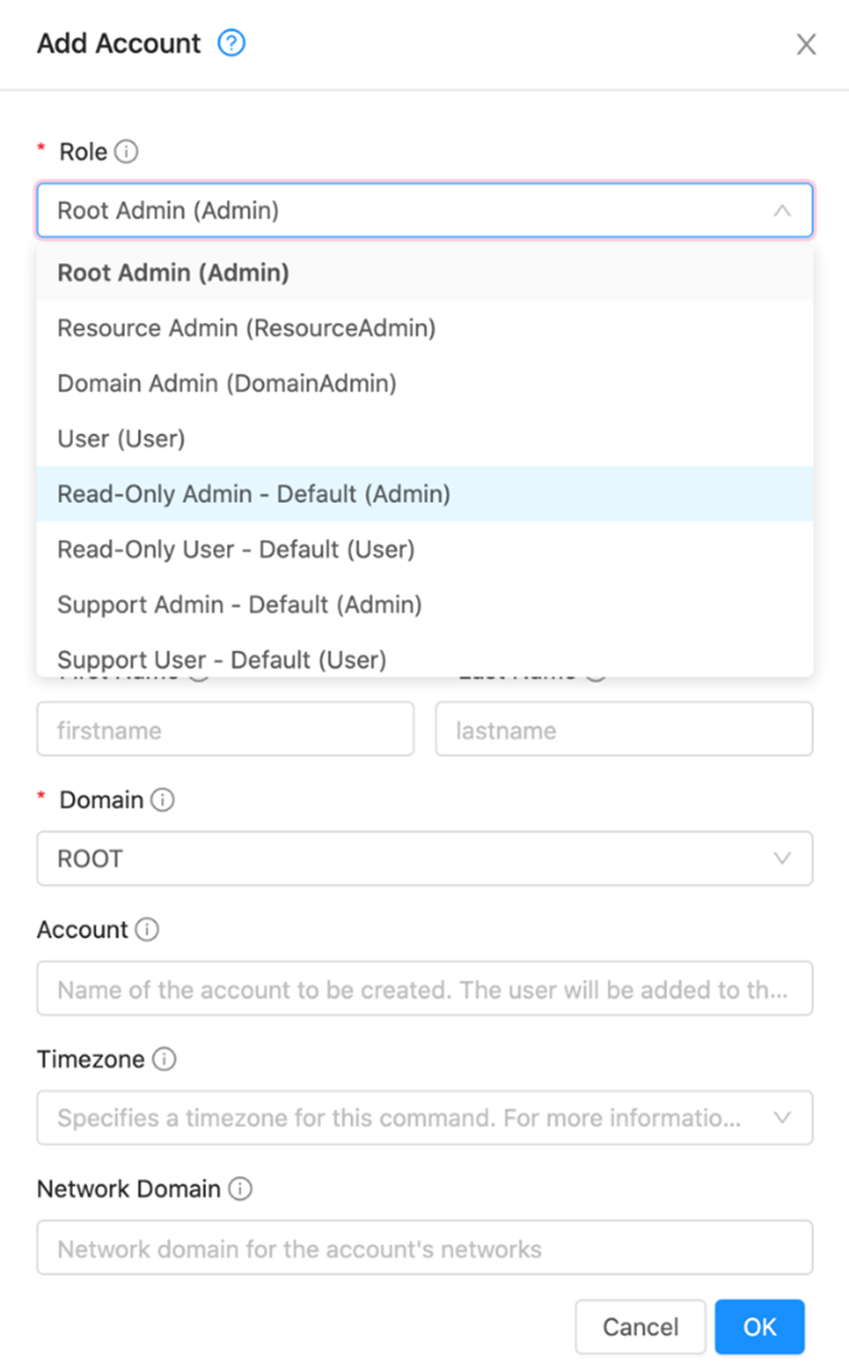
Any of these roles can be selected to create an account:
This feature will be included in Apache CloudStack 4.15, which is an LTS release.
Suresh Anaparti has over 15 years of end-to-end product development experience in Cloud Infrastructure, Telecom and Geospatial technologies. He is an active Apache CloudStack committer. He has been working on CloudStack development for more than 5 years.
You can learn more about Suresh and his background by reading his Meet The Team blog.